How to avoid WebRTC still leaking the real IP when using a proxy? Attached solution
 2025.03.03 06:56
2025.03.03 06:56Have you ever noticed that when you use a proxy server to browse the web, the WebRTC (Web Real-Time Communication) protocol may reveal your real IP address? This is because WebRTC is enabled by default in some browsers and can be directly accessed through JavaScript scripts Obtain your local IP address. Although this may sound a bit worrying, we should not lose faith in proxy technology. Proxies continue to be a very useful tool for protecting our privacy and security online. It’s just that we need to realize that proxies are not 100% reliable, so we need to take other additional measures to protect our privacy and security, such as anti-detection of browsers.
Introduction to WebRTC:

WebRTC is a real-time communication solution initiated by Google, which includes video and audio collection, encoding and decoding, data transmission, audio and video display and other functions without the need for an intermediate server (after the connection has been established). WebRTC features:
1. Free, whether for personal or commercial use.
2. Has cross-platform compatibility and supports all major browsers
3. Suitable for mobile applications
4. It provides better sound quality compared to Flash with adjustable built-in microphone settings
5. Able to integrate seamlessly with existing communication protocols and APIs
6. Provide a high degree of security, including end-to-end encryption
The principle of WebRTC leaking real IP is as follows:
WebRTC supports the direct establishment of point-to-point connections between browsers to achieve real-time communication, such as video, voice and data transmission. When establishing a WebRTC connection, the browser transmits its IP address to the other party to facilitate a successful connection between the two parties. An attacker can use JavaScript or other technologies to access the API in WebRTC to obtain the user's IP address.
WebRTC’s STUN/TURN server can also leak the user’s IP address. The STUN/TURN server is a key component in WebRTC for NAT traversal and relay. If these servers are vulnerable or misconfigured, attackers can use them to obtain users' real IP addresses, thereby posing a threat.
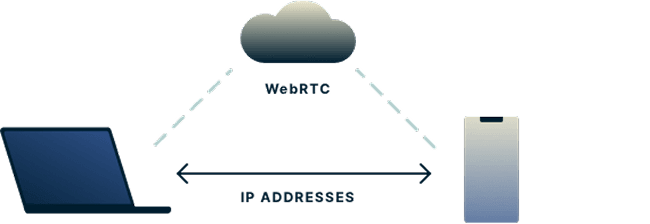
What does a WebRTC leak mean?
WebRTC leakage refers to the visibility of IP addresses, which brings greater security risks to end users. WebRTC leaks can occur when you want to communicate video or audio with others through a browser that uses WebRTC technology. At this point, the browser exposes your IP address, which is why it's called a "leak." WebRTC leaks threaten those who wish to keep their online identities anonymous.
How to confirm whether the browser will leak the real IP through WebRTC?
Check WebRTC status
First, you can manually check the browser's WebRTC status. In Chrome, you can type chrome://flags/#disable-WebRTC in the address bar and check the relevant settings to confirm whether WebRTC has been activated. In Firefox, you can enter about:config in the address bar, search for media.peerconnection.enabled, and confirm whether its value is false. This value means that WebRTC has been disabled.
Use online detection tools
Second, a more convenient way is to use online detection tools. Such tools are specifically designed to detect whether your browser has WebRTC leaks. Visiting the websites of these tools to start the detection process often only requires the click of a button. The tool will try to obtain your IP address through WebRTC's API. If your public and private IP addresses are displayed after connecting to VPN/IP, this indicates that the browser is at risk of leakage.
Note: If you frequently use multiple browsers, you should consider testing on each browser to see if there is a possibility that WebRTC will leak your real IP.
How to prevent WebRTC leaks?
1. Manually disable WebRTC in the browser to prevent leaks.
To disable WebRTC in Firefox, enter about:config in the address bar, click the "I accept the risk" button, search for media.peerconnection.enabled and double-click to change the "value" to "false".
Chrome can disable WebRTC through two extensions, uBlock Origin and WebRTC Network Limiter.
Safari does not need to disable WebRTC. Its permission model is strict. By default, the website will not provide other IP addresses except the IP address for accessing the website.
In the desktop version of Opera, open Settings, expand "Privacy and Security" in "Advanced", scroll to WebRTC, select the Disable non-proxy UDP radio button and close the tab to save.
Microsoft Edge currently cannot completely disable WebRTC, but you can enter about:flags in the address bar and select the "Hide local IP address through WebRTC connection" option to hide the local IP address.
2. Use a dedicated VPN
Choose a VPN service that provides WebRTC leak protection, and make sure this feature is enabled by default on all servers. Or: Choose a VPN service that offers WebRTC leak protection and make sure it turns this feature on by default on all servers.
3. Use anti-detection browsers
Anti-detection browsers can be called the best solution to WebRTC related problems. BitBrowser can truly simulate the underlying data to control WebRTC fingerprint data, avoiding the leakage of real IP addresses and the use of JavaScript to modify this Different from the surface-level methods, BitBrowser handles the processing from the bottom layer of the browser. It is compiled based on Chrome and Firefox kernels and modifies the API so that the information obtained at the JavaScript layer is not unique. Even if WebRTC is enabled, it cannot leak your real IP address.
BitBrowser supports four modification modes:
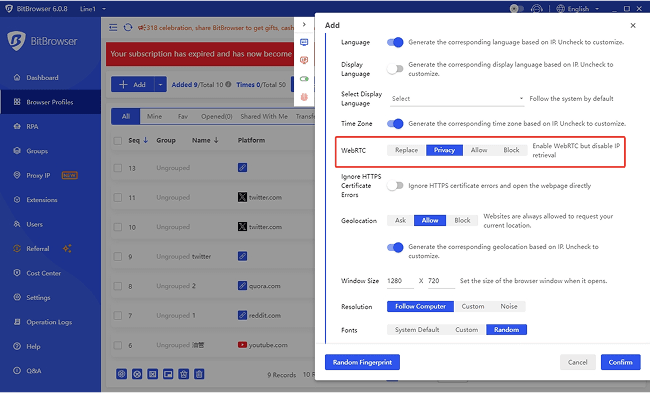
Change mode – enable WebRTC, replace the public IP with the proxy IP, and mask the local IP
Disabled mode – WebRTC is turned off and the website will detect that you have turned off WebRTC
Privacy mode – Enable WebRTC, but prohibit IP acquisition
Real mode – Turn on WebRTC, the real IP of the current computer will be used
Summarize:
This article introduces WebRTC, as well as the principle of WebRTC leaking real IP and how to detect whether WebRTC leaks real IP and how to prevent it. Although WebRTC brings certain security risks, its convenient real-time communication capabilities are also extremely convenient. Our lives have changed. For those who need to remain anonymous on the Internet, you might as well try using BitBrowser with a proxy IP to protect your security and privacy. Even if WebRTC is turned on, BitBrowser can still protect your real IP. If it is stolen by someone with intentions, prevent it from being used against you.
common problem:
Question: What are the main functions of WebRTC?
Answer: It includes audio and video calling, screen sharing, data transmission and other functions.
Question: What scenarios is WebRTC suitable for?
Answer: It is suitable for video conferencing, online education, real-time customer service and other scenarios.
Question: Does WebRTC require a plug-in?
Answer: Usually no additional plug-ins are required and can be used directly in modern browsers.
Question: Is it difficult to use WebRTC in development?
Answer: There is some complexity, but there are many open source libraries and tools to help with development.
 BitBrowser
BitBrowser
 Multi-Account Management
Multi-Account Management Prevent Account Association
Prevent Account Association Multi-Employee Management
Multi-Employee Management