Shared Browser profiles And Security Lock
In scenarios involving multi-account management and team collaboration, "Shared Browser profiles" and "Security Lock" are the core features of BitBrowser that enhance efficiency and ensure security. The former enables cross-user sharing of browser windows, while the latter builds a multi-level account protection system. Below is a detailed explanation of the features and an operation guide:
I. Shared Browser profiles:
Advantages of Browser profiles Sharing:
◆ Enhanced Team Collaboration Efficiency: Supports quick sharing of configured browser windows (including parameters such as fingerprints, proxies, and extensions) with team members, eliminating redundant configurations
◆ Secure Isolated Sharing: Data of shared windows is independently encrypted. Recipients can only use the preset Browser profiles and cannot modify core configurations
Operation Process:
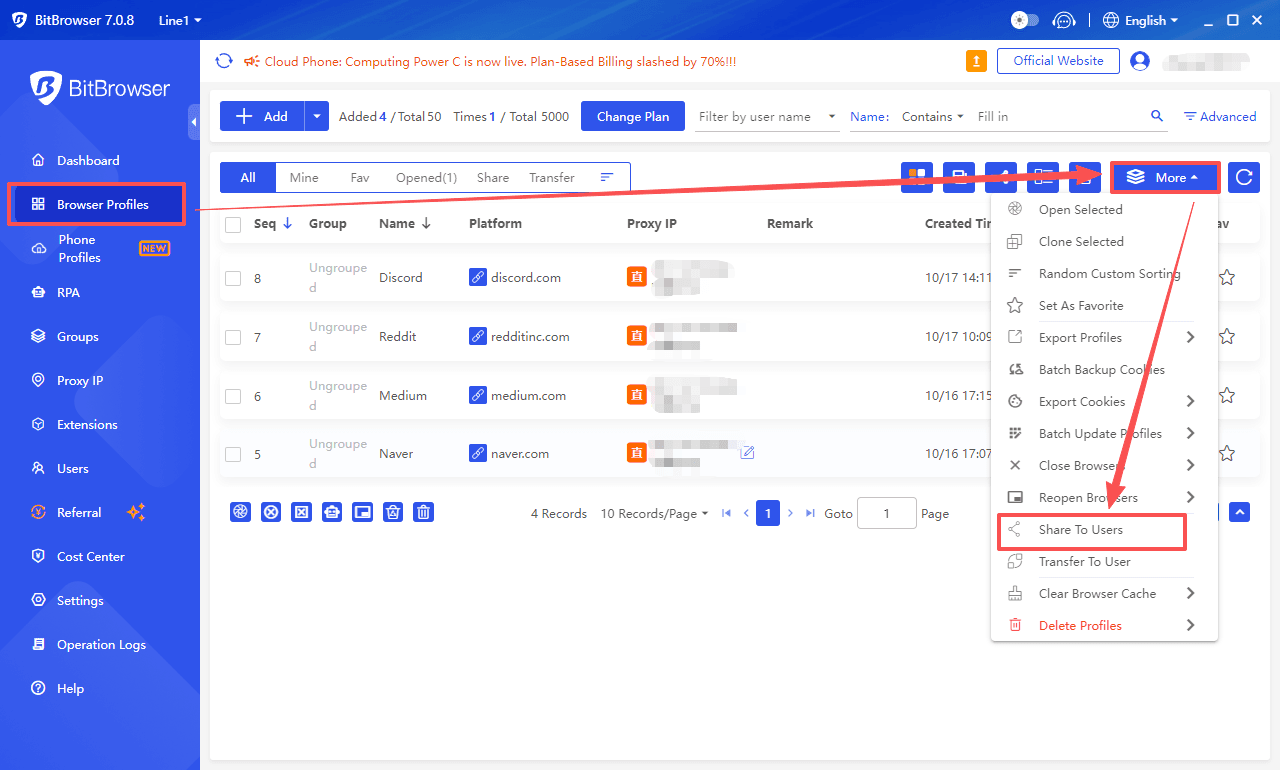
1. Select the Target Window:
Open BitBrowser and find the window to be shared in the "Browser Windows" list (single or batch selection is supported).
2. Access Sharing Settings:
Click the "More Operations" button (three-dot icon) on the right side of the window and select "Share Browser profiles".
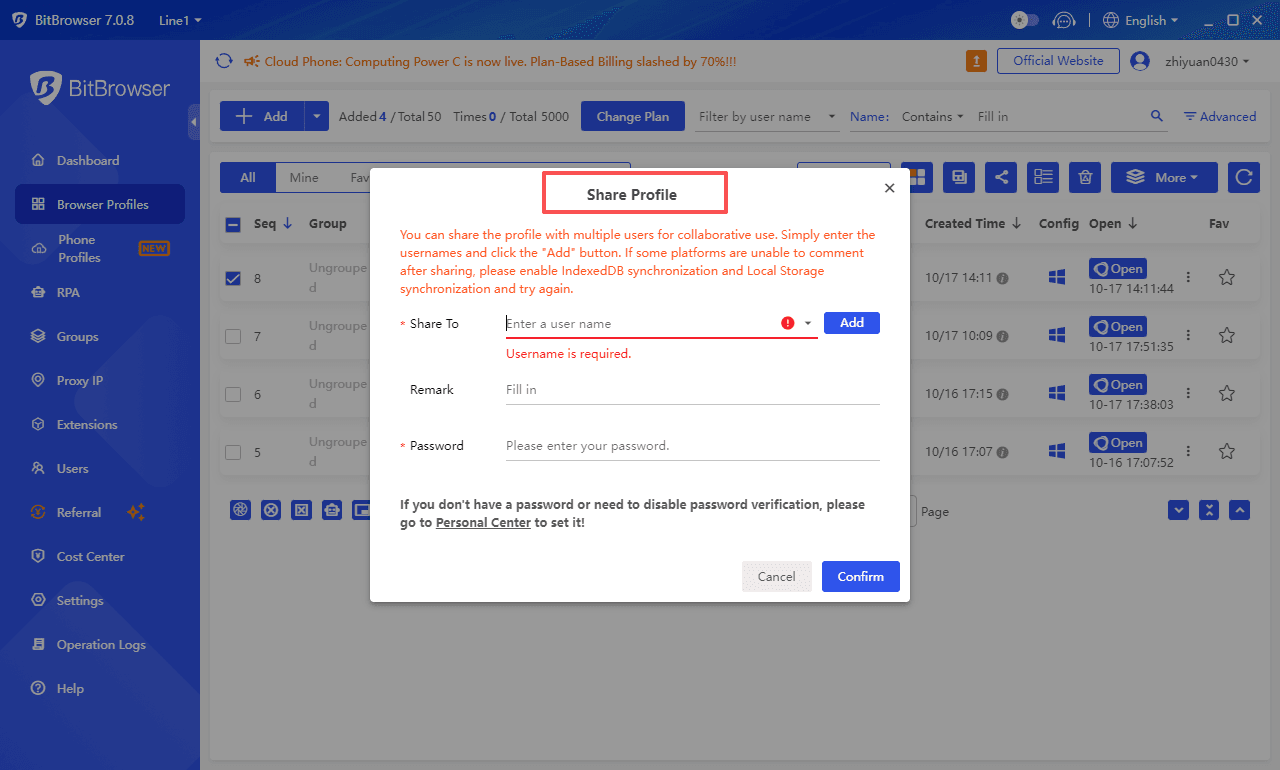
3. Configure Sharing Permissions:
Recipient Type: You can select team members (directly from the "Employee Management" list) or generate a temporary sharing code (supports setting a validity period of 7/15/30 days).
Permission Scope: Basic permissions only allow using the window Browser profiles (modification of fingerprints/proxies is prohibited), while collaboration permissions can enable "Browser profiles Fine-Tuning" (authorization should be granted with caution).
4. Generate Sharing Link/Invitation:
Internal team sharing is directly linked to sub-accounts; external sharing generates a password-protected link, and the validity period can be customized.
5. Recipient Confirms Usage:
Team members enable the window in the "Shared Windows" list; external collaborators enter the password via the link to automatically load the Browser profiles.
II. Security Lock: Comprehensive Account Protection System
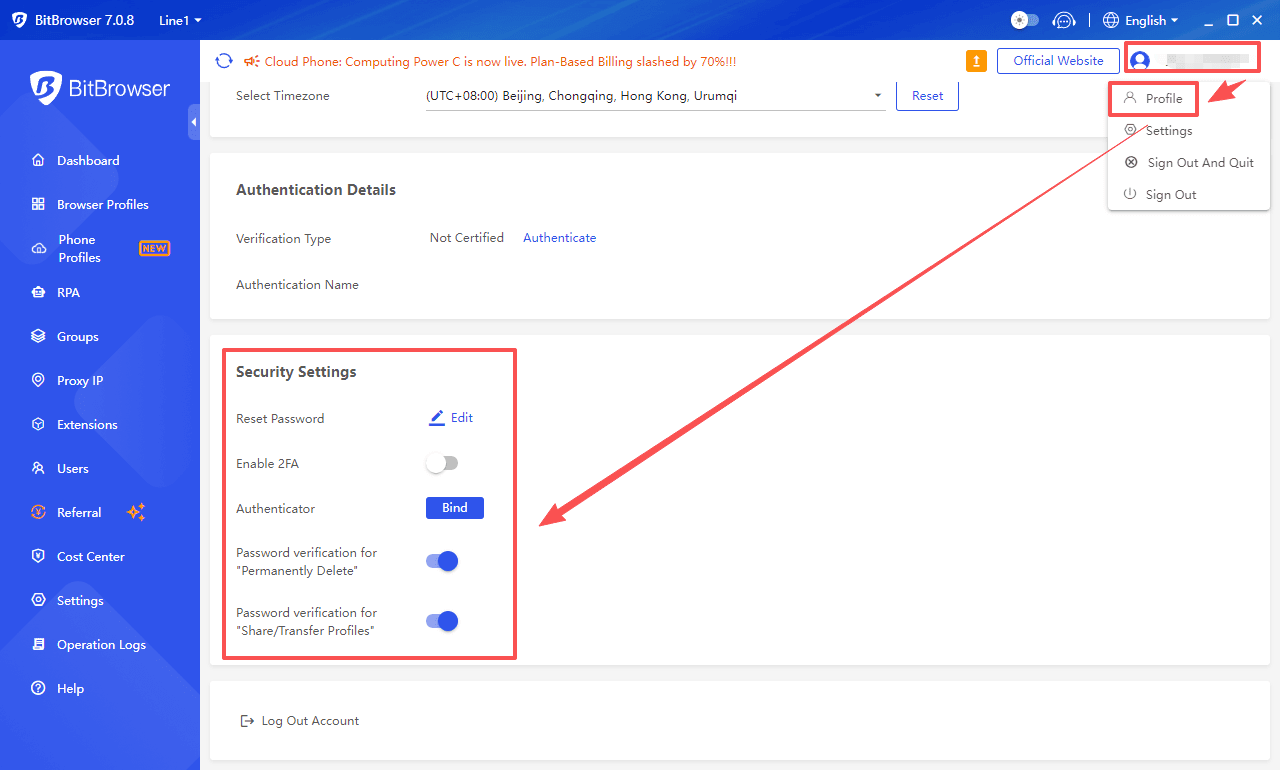
1. Two-Factor Authentication (2FA): Account Login Protection
Activation Steps
Security Advantages
★ Even if the password is leaked, login is not possible without the verification device;
★ Multi-device binding is supported (up to 3 frequently used devices can bypass verification; new devices require dynamic code verification).
2. Password and Account Protection
Password Management
★ Password Modification: Go to "Personal Center" → "Password Settings" to modify the password using the original password or reset it via mobile phone/email verification code (an 8-16 character complex password is required).
★ Password Retrieval: Click "Forgot Password" on the login page, obtain a verification code via the bound mobile phone/email, and username retrieval is supported (aided by the "Retrieve Username" function).
3. Device and Browser profiles Security
★ Login Security Lock: Automatically sends an alert when an unusual login from a different location is detected (notifications need to be enabled in security settings). It supports manual logout of abnormal devices or setting automatic screen lock (after 10 minutes of inactivity).
★ Encrypted Data Storage: Data of shared windows is encrypted with AES-256, HTTPS protocol is used for transmission, and locally stored sensitive data is linked to the user's unique key to prevent unauthorized access.
III. Common Issues and Solutions
1. Can I restrict recipients from modifying configurations when sharing an Browser profiles?
Yes. Select "Basic Permissions" in the sharing permission settings – recipients can only use preset configurations such as fingerprints, proxies, and extensions, and cannot modify core parameters. If collaborative modification is needed, "Collaboration Permissions" can be enabled, but it is recommended to only open this to trusted members.
2. What two-factor authentication methods does Security Lock support?
Three methods are supported: mobile SMS verification code, one-time email password, and third-party verification apps (e.g., Google Authenticator, Microsoft Authenticator). Third-party apps are recommended as they do not rely on a network connection and can generate dynamic codes offline.
3. What should I do if I forget my 2FA-bound device?
If the bound mobile phone/email is invalid, you can log in using the pre-saved backup verification code through the "Emergency Recovery" function in "Security Settings".
4. Will window data shared among team members affect each other?
No. Each shared window has an independent cache, cookies, and fingerprint environment. Operations performed by recipients only affect their own instances. The original window data is fully controlled by the sharer, who can revoke permissions at any time.
5. Will the login process become more complicated after enabling Security Lock?
Device binding is required during initial setup. For subsequent logins, an additional dynamic code verification step is added after entering the password (taking approximately 10 seconds).
Summary: By using "Shared Browser profiles" and "Security Lock" together, BitBrowser achieves in-depth integration of collaborative convenience and security protection: Teams can quickly reuse mature browser Browser profiles configurations to reduce repetitive work; Mechanisms such as two-factor authentication and device locking prevent account and data leakage, ensuring the security of core information even in shared Browser profiles. Whether for multi-store collaboration in cross-border e-commerce teams or multi-account management for individual users, these two features can provide reliable support for business operations, making collaboration more efficient and security more controllable.