Team Management / Member Authorization
In team collaboration scenarios, refined Permission Management is the core to ensuring account security and efficiency. BitBrowser enables flexible permission allocation through a "Role System", supporting the creation of custom roles based on business needs to precisely control the operation scope of different members. Below is the full-process operation from role creation to permission configuration:
1. Role Creation: Building the Team Permission Structure
Operation Entry: Client → Left Menu "Employee Management" → Click the "Add Role" button
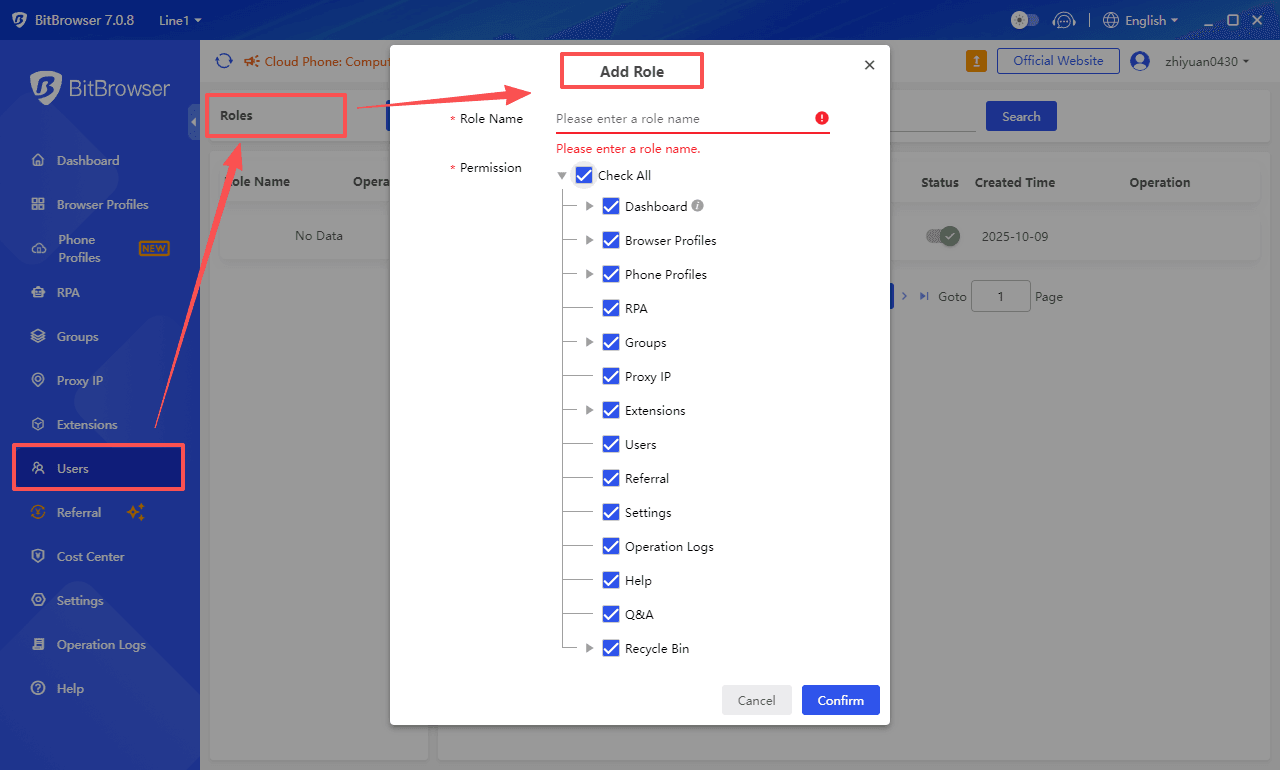
1.1 Define Role Name (Required)
Set role names according to team division of labor, for example:
Business Line Roles: Amazon Operations, Shopee Store Manager, Facebook Advertising Specialist
Functional Roles: Audit Supervisor, Data Analyst, Permission Administrator
1.2 Configure Permission Matrix
Click "Permission Management" to enter the 4-dimensional permission configuration interface, supporting modular breakdown:
| Permission Module | Basic Operations (Recommended to Open) | High-Risk Operations (Open with Caution) | Recommended Strategy |
|---|---|---|---|
| Browser Window Management | Create/Edit Windows, Batch Import | Delete Windows, Copy Others' Windows | Only open "Own Window Operations" for members |
| Advanced Permissions | Fingerprint Configuration, Proxy IP Settings | Batch Export Cookies, Modify Global Fingerprint | Limited to Administrator/Manager roles |
| Group Management | Allow Creation of Sub-Groups | Set Data Retention Period (e.g., 7 days) | Allocate functions according to department needs. |
| Function Module Control | Allow Installation of Product Selection Tools, SEO Plugins | Enable "Scheduled Product Listing" and "Batch Reviews" | Open on demand; the Extension Center and automated tasks are subject to package permissions. |
1.3 Save and Manage Roles
- Click "Confirm" to complete the creation; you can modify the configuration at any time via the "Pencil Icon".
Inactive roles can be removed via the "Delete Icon" (all associated users must be unlinked first).
2. Permission Allocation: Three Core Roles
BitBrowser presets a three-level identity system, supporting custom expansion based on this system:
2.1 Administrator
| Permission Scope | Core Functions | Applicable Scenarios |
|---|---|---|
| Global Control | Employee Account Management, System Settings, Modify Package Configuration, Audit Operation Logs. | Enterprise Main Account, IT Administrator (recommended for only 1-2 people) |
| Data Permissions | View window data of all groups, export full operation logs. | |
2.2 Manager
| Permission Scope | Core Functions | Collaboration Value |
|---|---|---|
| Subordinate Management | Manage employees within the group, adjust role permissions (within authorized scope). | Batch export team window configurations (including cookies, proxy IPs, etc.). |
| Group Management | Create department-specific groups, configure shared fingerprint templates within the group. | Sync commonly used plugins to subordinate members' accounts. |
2.3 Member
| Permission Scope | Core Functions | Operation Restrictions |
|---|---|---|
| Basic Permissions | Window Operations (Create Own Windows, Import Cookies), Enable Automated Scripts. | Can only manage windows within authorized groups; cannot view data of other departments. |
| Operation Restrictions | Prohibited from modifying proxy IP policies and core parameters of browser fingerprints. (Permissions can be manually assigned) | |
3. User-Role Binding: Quickly Build Team Structure
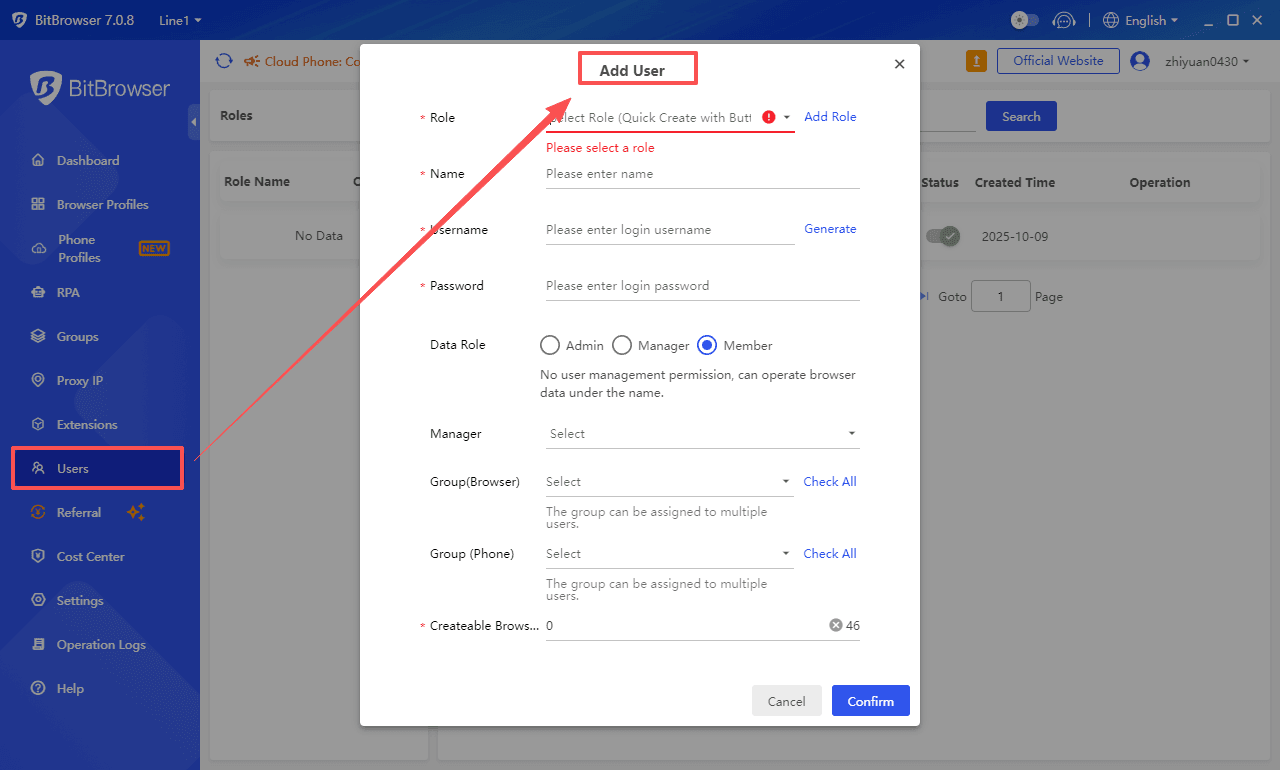
Operation Entry: Client → Left Menu "Employee Management" → Click "Add User" → Select Target Role
Key Configuration Item Description
| Configuration Item | Description | Key Points |
|---|---|---|
| Role Association | Select a created role from the drop-down menu. | Supports quick jump to create a role if none exists. |
| Authorized Groups | Check the groups that can be managed (multiple selections supported). | Members can only operate on the checked groups. |
| Window Quota | Set the number of windows that can be created. | Subject to the main account package limits; for example, the Basic Package limits 50 windows per user. |
Overview of Management Operations
| Function Icon | Operation Description |
|---|---|
| Circle | Quickly jump to the authorized group window page of the user. |
| Pencil | Modify user information such as name, role, and authorized groups. |
| Delete | Remove employee account (must disable and reclaim permissions first). |
| Lock | Reset login password (supports forcing the user to change it at next login). |
| Status | Enable/Disable account (temporarily freeze unauthorized access). |
4. Common Issues and Solutions
4.1 Unable to Recover Important Window Data Deleted by Employees by Mistake?
Issue Performance: Members accidentally delete core business windows, and there are no records in the recycle bin.
Solution:
Administrators enable "Secondary Verification for Window Deletion" (verification code required for high-risk operations).
Adjust recycle bin permissions: Open "Permanently Retain Deletion Records" for roles above Manager; members can only retain recoverable data within 30 days.
Regularly back up core configurations through the "Batch Export Windows" function.
4.2 Prompt "Associated Users Exist" When Role Deletion Fails?
Issue Performance: When deleting an inactive role, the system prompts "There are 5 associated users under this role".
Solution:
Batch Transfer Users: Check the associated users in the "Employee Management" list and batch modify their roles (e.g., switch to "Default Role").
Individual User Handling: Click the "Pencil Icon" on the right side of the user, select another role from the role drop-down menu and save to unlink the original role.